[vc_row][vc_column][vc_single_image source=”featured_image” img_size=”full” style=”vc_box_rounded” css_animation=”bounceIn”][vc_column_text]When navigating cybersecurity, it’s clear there isn’t a one-size-fits-all approach in risk management. For instance, an engineer working with a team to control electrovalves has a different set of considerations than a developer designing video game consoles. Whether it’s a PLC, or a satellite – each technology demands its unique cybersecurity considerations. Understanding this distinction is the first step toward comprehensive protection.
When considering cybersecurity context and applications is the key, first assessing the environment in question. Does this device process data? How does it communicate? Comprehending these nuances helps pinpoint potential vulnerabilities.
Unique Cybersecurity Needs Across Diverse Technologies
One significant area requiring specialized focus is medical devices. The number of medical devices connected to networks is increasing. Years ago, only 20% of new medical devices were smart devices. Now, that number is closer to 50%, devices such as infusion pumps, CT scanners, MRI scanners, ultrasound devices, X-ray machines, patient monitoring systems, point of care analyzers, nurse call stations, and more, all with different: functionalities, hardware, operating systems, applications, protocols, and even different human interactions, it’s challenging to have a single security mechanism for all these devices.
Unlike cell phones or laptops that are replaced frequently, medical devices, like points of care, have a lifespan of 8-10 years. Legacy devices pose risks because they may not be equipped to deal with new threats. That is why risk assessment forms the foundation of a robust system. For instance, the risks a satellite engineer encounters differ from those a PLC engineer might. From a developmental perspective, assessing a mid-range controller isn’t the same as evaluating a high-end one. But by unpacking these risks, one can preempt potential pitfalls.
The Cyber-Physical Landscape
In the IoT (Internet of Things) setting, we’re using systems that combine both digital and physical elements, known as Cyber-physical systems (CPS). We shouldn’t use the same security everywhere because it can disrupt how things work. Instead, the approach should be tailored, factoring in the potential impact and exposure level for each case.
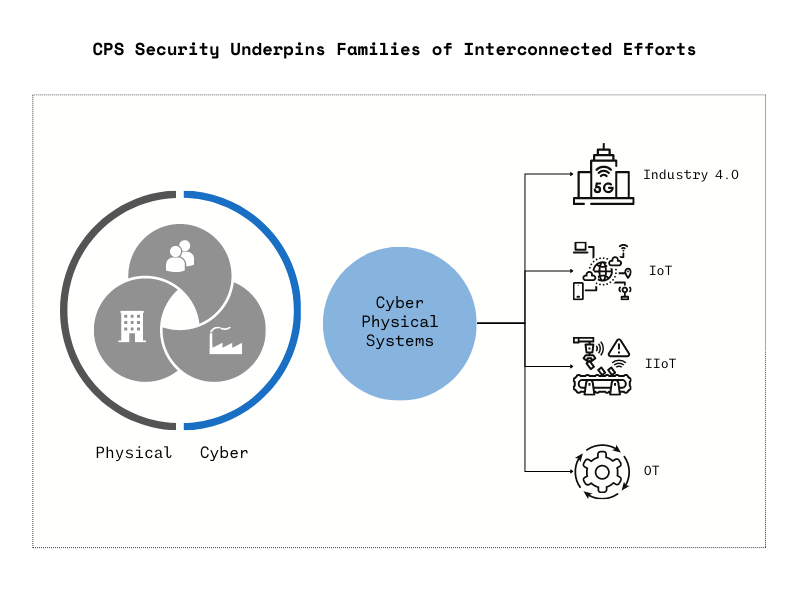
Here are a few terms you might have heard but perhaps are unfamiliar with:
- OT (Operational Technology): This involves specialized hardware and software designed to detect or cause changes in physical processes by directly monitoring or controlling devices such as valves and pumps.
- IoT (Internet of Things): This system consists of interconnected computer devices, machines, objects, animals, or people. These entities have unique identifiers (UID) and can transfer data over a network without requiring direct human-to-human or human-to-computer interactions.
- IIoT (Industrial Internet of Things): This encompasses a network of sensors and other devices combined with industrial computer applications. By interlinking these devices, data collection, exchange, and analysis are facilitated, enhancing industrial operations’ productivity and efficiency.
- CPS (Cyber-physical system): A CPS fuses computers and networks with physical processes. While IoT emphasizes devices communicating over the internet to gather and share data, a CPS integrates physical and computational components for controlling more complex systems. For instance, in a factory setting, by interconnecting machines and sensors, a CPS gathers data, anticipates failures, and optimizes processes, bolstering productivity.
- Vulnerability: It refers to a system’s inability to withstand adverse environments. A “window of vulnerability” is a time frame during which defensive measures are reduced or missing.
- Threat: A potential danger that could exploit a vulnerability, compromising security.
- Risk: Risk is computed as the product of the threat, vulnerability, and consequence. It evaluates the likelihood of a threat exploiting a vulnerability, resulting in specific damage.
The rise of IoT in various environments, from workplaces to homes, intensifies the interaction with CPS. This interplay magnifies potential consequences. If interference occurs in predictive maintenance, undetected failures could entail substantial repercussions, including financial losses and regulatory issues.
Incorporating cognitive computing and AI is revolutionizing technologies. However, this innovation amplifies complexity and the attack surface in cybersecurity.
The automation and interconnectedness surge, fueled by the expansion of IoT and CPS, pose significant security challenges. Such concerns are especially drastic in critical settings like hospitals, where these connected devices could jeopardize patient lives and the overall healthcare system.
Just a few days ago, Prospect Medical Holdings, a company that owns more than 170 medical facilities, reported that it took its national computer systems offline after discovering a cyberattack. According to BBC News this is the biggest cyberattack in the healthcare system in years.
As we advance in this digital age, cybersecurity becomes increasingly crucial. Protecting systems, data, and people’s privacy has never been more urgent.
Striking a Balance in Automation
Now, let’s go into closed-loop systems. Consider a relatable example: adjusting the water temperature when taking a shower in cold weather. Here, your body acts as a sensor, modulating the water temperature – a clear representation of a closed-loop system in action.
Automation risks with IoT tie back to these closed-loop systems. Leading providers often opt for predictive systems over closed loops. For instance, SKF might produce a report based on data from vibration sensors on pumps. Similarly, power-generation turbines from giants like GE and Siemens utilize predictive maintenance systems. The rationale behind this choice stems from potential risks associated with closed loops in IoT devices. Incorrect value inputs could pose significant threats, making closed-loop systems in IoT equipment a less recommended option.
Recent Discoveries:
I recently watched a video focusing on the current state of vulnerabilities due to electromagnetic wave emissions in modern information systems. Detecting and analyzing these emissions uncovers security and privacy weak spots. Knowledgeable individuals equipped with electromagnetic theory, programming skills, and affordable hardware tools like SDR can exploit these vulnerabilities. The study first delves into VGA interface emissions and later transitions to HDMI interface emissions.
Learn more about HDMI emissions
In conclusion, as technology evolves, it’s essential to stay informed, vigilant, and proactive in addressing cybersecurity challenges, with expert guidance and a thorough understanding, navigating it becomes manageable.
[/vc_column_text][/vc_column][/vc_row]


